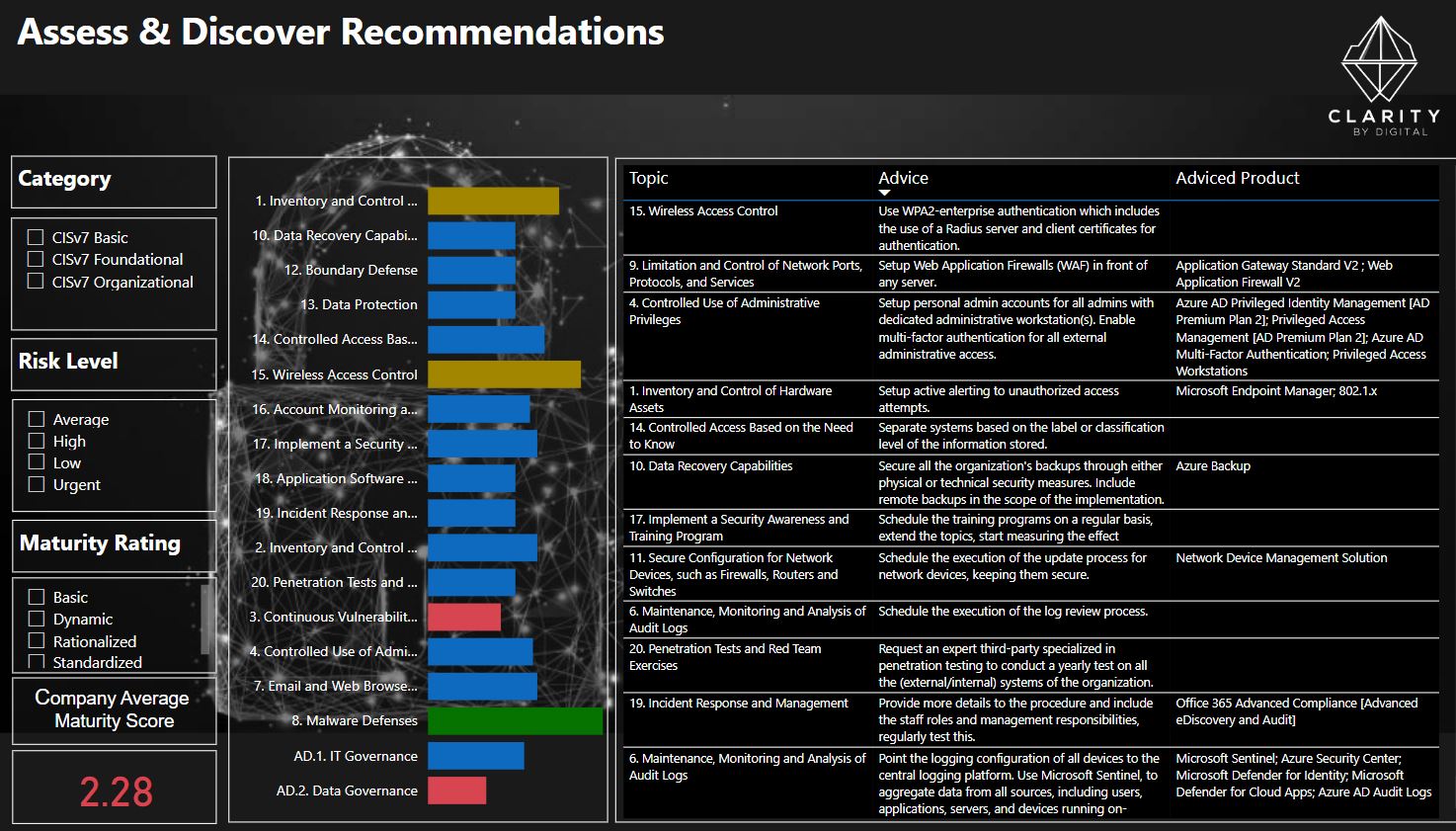
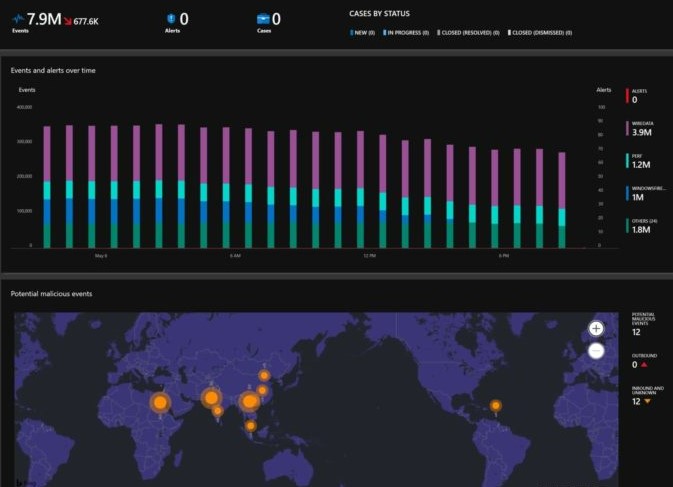
The Security Issue
SonicWall’s 2022 Cyber Threat Report concludes the logging of 5.4 billion malware attacks in 2021, making it the second highest attack type by total volume. The number of encrypted threats spiked by 167% (10.4 million attacks), ransomware rose by 105% to 623.3 million attacks, cryptojacking rose by 19% (97.1 million attacks), intrusion attempts by 11% (a whopping 5.3 trillion) and IoT malware rose by 6% to 60.1 million attacks. In security, there is no average behavior.
Security issues organisations are facing include:
– Dwell time around 141 days for an organisation to detect a security incident
– Increasing number of vulnerabilities and public exploits
– Lower barrier to entry for adversaries to conduct attacks
– Increased number of attacks for financially motivated attackers
– Not enough skilled security professionals to support strategic, tactical and operational roles